The roll-out of COVID-19 vaccinations is accelerating, with around 250 million doses already administered globally and millions more receiving their injections daily. But while this worldwide vaccination program is truly unprecedented, it’s worth remembering that less than 1% of the world’s population has received their full course of injections. Billions of people are still waiting for their first dose – which inevitably leads those people to question when they are likely to receive it, which of the many available vaccines they are likely to get, what the possible side effects of the different vaccines are, and more.
To get answers to these questions, they will search the web. And unfortunately, scammers and criminals are already alert to this thirst for information, and are looking to exploit it for their own malicious purposes.
One of the surest signs of imminent online scams is an increase in domain registrations. This signals that scammers are preparing web content, which appears to be genuine in order to attract curious people, with the aim of stealing their credentials and account details, or stealthily installing malware on their PCs or devices. All it takes is for an unwary person to key in details, such as their email address and password, and the scammer could then have the keys to one or more of that person’s private or work accounts – which they can then sell on, or exploit for their own profit.
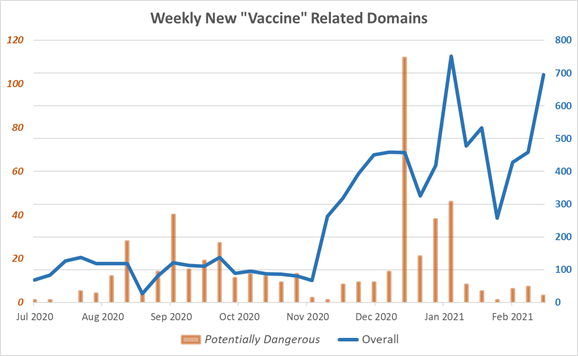
Check Point Research (CPR) confirms that the number of domains featuring the word “vaccine” in their title has significantly increased over the past 4 months, as the global vaccine rollout was being prepared and launched. Since the beginning of November 2020, until now, CPR documented 7,056 new vaccine-related domains, of which 294 domains were deemed potentially dangerous.
Compared to the previous period between July and October, CPR documented only 1,773 new domains, where 228 were deemed potentially dangerous. In effect, domain registrations increased by 300% throughout the two time periods, while websites deemed dangerous by CPR increased by 29%.
To illustrate how hackers are using COVID- related malicious domains, CPR has graphed below the number of “weekly new ‘vaccine’ related websites” between July 2020 and Feb 2021.
Example: Impersonating the U.S. CDC
Check Point Research (CPR) recently uncovered an example of a malicious website, impersonating the U.S. Centers for Disease Control and Prevention (CDC). The malicious website asks a visitor to key in their Microsoft credentials.
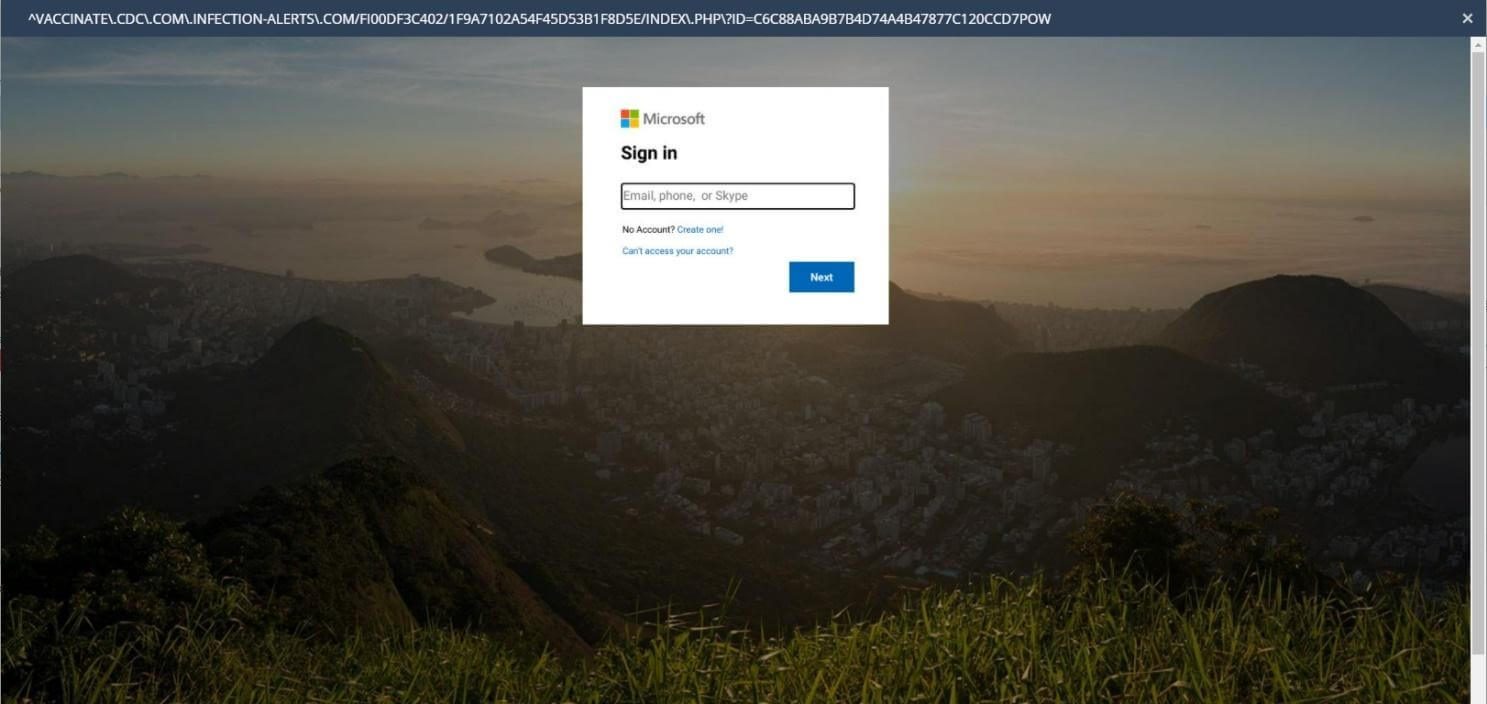
Although the main domain (infection-alerts.com) was created in April 2020, CPR believes its sub-domains were created recently. Browsing to this malicious website was first spotted in late January 2021, and a few weeks before, there was another similar subdomain used by hackers – covid19.vaccine.infection-alerts.com, which is now inactive.
CPR expects the vaccine related scams to continue in the near-term future, and we advise people everywhere to watch out for and learn how to protect themselves against phishing and domain spoofing attacks.
How to stay protected
- Watch for misspellings – Beware of misspellings or sites using a different top-level domain. For example, a .co instead of .com. Misspelling in domains are a string giveaway that deception is at play.
- Beware of “buy vaccines online” offers – As tempting as it may be while many of us wait to receive our vaccinations, these offers are virtually guaranteed to be a scam.
- Never share your credentials – Credential theft is a common goal of cyberattacks. Many people reuse the same usernames and passwords across many different accounts, so stealing the credentials for a single account is likely to give an attacker access to a number of the user’s online accounts. Never share your account credentials and don’t re-use passwords.
- Always be suspicious of password reset emails – If you receive an unsolicited password reset email, always visit the website directly (don’t click on embedded links) and change your password to something different on that site (and any other sites with the same password). By clicking on a link, you can reset the password to that account to something new. Not knowing your password is, of course, also the problem that cybercriminals face when trying to gain access to your online accounts. By sending a fake password reset email that directs you to a lookalike phishing site, they can convince you to type in your account credentials and send those to them.
- Always note the language in the email – Social engineering techniques are designed to take advantage of human nature. This includes the fact that people are more likely to make mistakes when they’re in a hurry and are inclined to follow the orders of people in positions of authority. Phishing attacks commonly use these techniques to convince their targets to ignore their potential suspicions about an email and click on a link or open an attachment.

